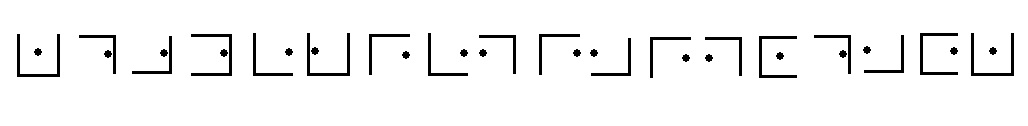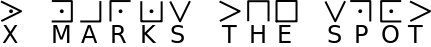Can You Decode These Messages?
Most people have at some time wished to find a way of writing in a code that nobody except themselves
could understand (for example, students writing notes during math class!). There are several ways of
attempting this. The simplest codes are based on swapping letters (a certain letter is replaced by
another letter). The decoder begins with the letter that occurs most often (in English, French, and
German, it is the letter E; in Spanish, it is the letter O).
Much more difficult to solve is a code that needs a special key. During World War II, the following
method was used. The people writing to each other possessed identical copies of a book. Each letter
was shown as a fraction, giving the page number and the number of the letter on that page. For
example, 87/15 meant the fifteenth letter on the eighty-seventh page. Write a coded message using your
math book (since we all bring our books to class every day!).
Another easily remembered code is to write a simple sign for each individual letter, using the following
arrangement:
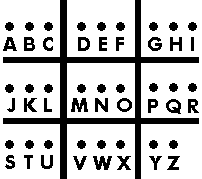
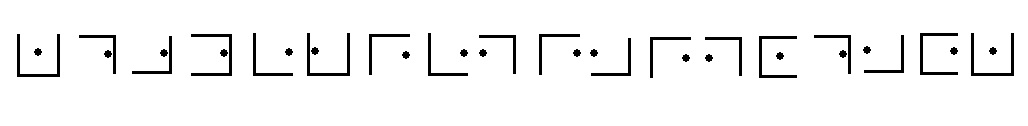
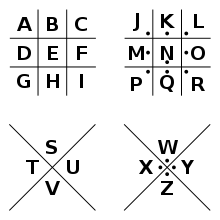
Another cipher that is similar to this one is the pigpen cipher (sometimes referred to as the Masonic cipher, Freemason's cipher, or tic-tac-toe cipher). It is a geometric simple substitution cipher which exchanges letters for symbols which are fragments of a grid just like the grid above. Here is one way the letters can be assigned to the grid:
Here is the code for “X marks the spot”:
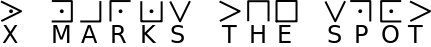
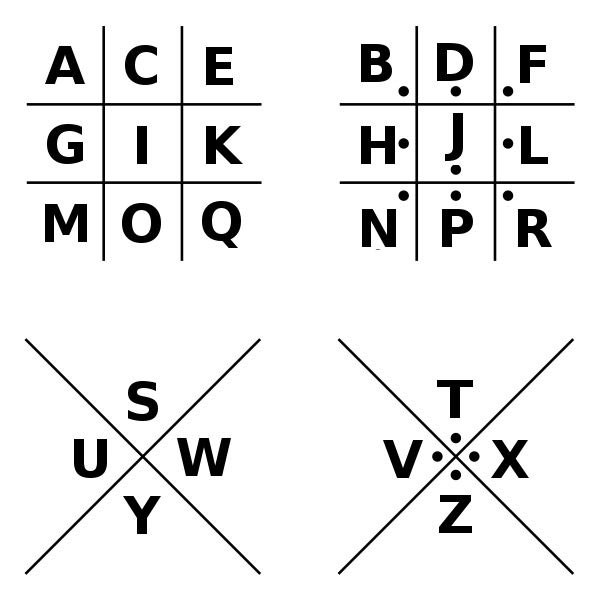
The Pigpen cipher has been used in several works of popular culture including Dan Brown's 2009 novel The Lost Symbol, on pages 164 and 184. In the game Assassin's Creed II, a variant of Pigpen is used to provide additional information about the story, in addition to Morse Code and binary code. Here is the variation of the Freemason cipher used in the computer game Assassin's Creed II:
Another type of code makes use of the alphabet circle. Each letter is replaced by the fifth one following it. A is replaced by F, B is replaced by G, and so on until U is replaced by Z; then V is replaced by A. This is illustrated conveniently by means of a circle:
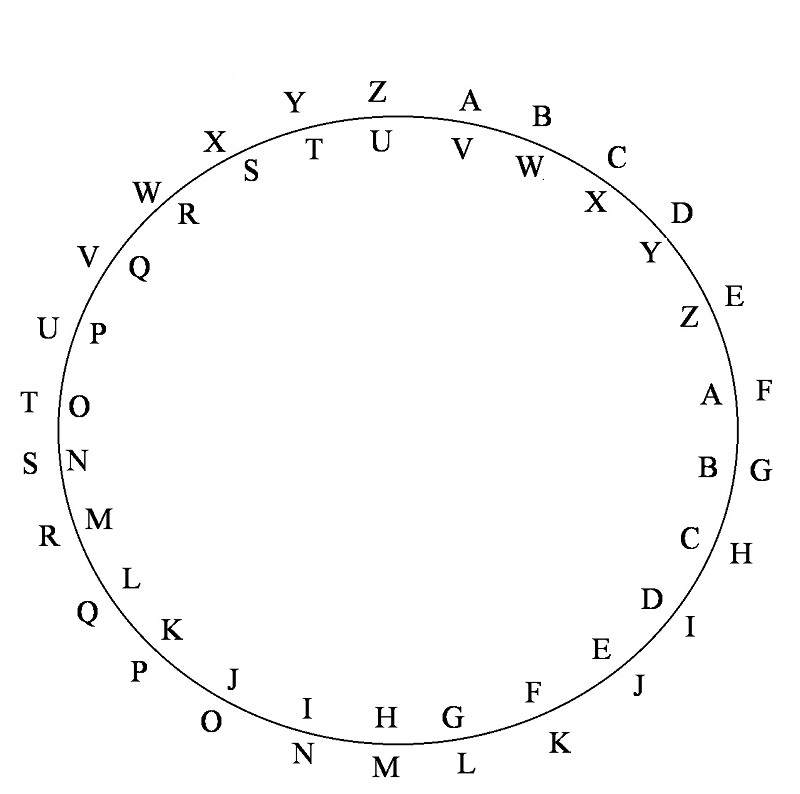
Use this key to code the message: Euclid has fallen arches.
Using the same key, decode this message:
YNRJ NX UFXXNSL … FWJ DTZ?
The Greeks used several kinds of codes. One of the simplest involves replacing letters by numbers. The letters are arranged as follows:
1 2 3 4 5
1 - f k p u
2 a - l q v
3 b g - r w
4 c h m - x
5 d i n s y
6 e j o t z
Every letter is given two numbers, one signifying the row it is in, the other the column. Putting the number for the row first, the letter C becomes 41. Using this key, code the following message:
TOMORROW WE WILL CHECK THIS WORK.
Another common form of code uses letters in which the order is changed. The letters are placed in some order that is known only by the two people concerned. Let us take a simple example:
AMY ELIZABETH (12 letters). Let us write it down in this form:
A Y L Z B T
M E I A E H
The correct message is obtained by reading from top to bottom.
Assignment:
(1) Construct your own code. Explain it in detail.
(2) Code one message using your secret code.